Cctv cameras
Upto 21Meg using MIPI interface on raspberry boards with Arducam(IMX477,219,179,298), Vision components(IMX296) and other modules from https://www.sony-semicon.co.jp/e/products/IS/security/product.html. See video Build USB Camera Module with image Sensor.
Neural networks
 |
https://www.upwork.com/hire/artificial-neural-networks-experts/ Rent neural expert to implement the github repos.
Robotics and drones
SRI abacus drive is a patented zero backlash drive system, easily manufactured and Patents hackable under South African law with a Fronting company . They are in parternship with Harmonic drive systems which is a difficult and expensive to manufacture high precision gearset which has close but not zero backlash. Harmonicdrive.net is squashing the abacus technology, the same way Texaco torpedoed NImH BatteryTech
Energy

Redrok solar links First published design of Fresnel solar array for a solar furnace. The Carnutt Solar Furnace as presented in "The Mother Earth News". Teton engineering extends the Carnutt furnace a design of 4x4m 6000watt concentrating heliostat.
These solar heliostats creates steam for a turbine, powering Claude cycle creating liquid nitrogen. Tankers delivers the offsite nitrogen from the solar fields for pumping into storage containers at residential homes(Cryogenic energy storage). The liquid nitrogen is released through a 150 degree celcius gas expansion chamber, driving a vehicle turbo charger for electricity generation. Compressed Air Engine as opposed to liquefied air transportation, doesn't have sufficient energy density to justify the tanker costs(liquid nitrogen is 700 atmospheres without the dangerous pressure, but the nitrogen containment vessel needs to free of brass for example or you wind up with a nitrogen bomb). Generating compressed air with heliostats 2x2m grids focused on PV cells on the roof is possible, but involves technical skill.(Each pv cell is covered in epoxy resin for waterproofing inside a glass cube and has ten suns focused on it as water is circulated for cooling.) Stirling Whispergen was a good solution but with only four suns focused on a pv cell has no technical or cost advantages, unless you use a MoltenSalt storage medium for night time power generation, which is impractical compared to the simplicity of Air Engines.
Focused suns, presents a fire hazard and insurance firms will take a dim view of the setup, hence the idea for cryogenic energy storage. The sun is for free and Reflective Material for the Fresnel blocks are around one ZAR per sqr. meter. What is holding all of this back is a cheap Solar Tracking device. Kipp & Zonen at 100,000 ZAR is only cost effective if the heliostats are ganged together with pivoting linkages, but the setup can't scale as the first linkage has to carry the strain of all the others and the tracker only manages 0.01 degree accuracy.

Fresnel design with lowest wind loading
https://storenergy.rs/ and storenergy.rs patent and similar design expired from solarcooking patents.

Another patent(svvti.com) on same conceptSolarLinks#Solar_ring expires Dec.2021.
. The svvti design is an inverted parabolic trough. Mirror slats directs the rays from above to a focal tube. Greenhouse uses this design to reduce solar flux inside. See venetian blinds type slat array svvti for more pictures. They all follow the same essential idea of first constructing a parabolic arc(inverted trough) and inserting the first mirror slat slightly to the left or right of the midpoint(highest) of the arc and aligning it to shine sunlight on the focul point below it. Next, the procedure is repeated to the left and right of this highest point with additional mirrors along the arc length. each mirror is oriented so it directs it light onto the same focul point as the previous mirror. The design is trivial to implement, without the need for precision tooling. Track the sun with the psa algorithm.

svvti.com, small pvc cells covered in epoxy and fixed to metal backplate with thermal paste. Water circulates for cooling
storenergy.rs design has the lowest wind loading of all known frensnel designs(Redrok solar links. Ceramic balls at the focal point are circulated in a loop with an auger screw mechanism heating the balls upto 900c. The balls are deposited into long steel tubes, generating super heated steam. Efficiency is much higher than molten salts(500c). Storenergy's fresnel design has the lowest wind loading but the large structure is only practical if a low cost tracking device isn't available due to the cubic cost size relationship. The Lazy Susan ring type platform with fresnel mirror blocks and counter weight design expires in April 2021. A small motor actuating a bicycle wheel steers it in the azimuth plane and is the most suitable design. The storenergy design is just easy to construct as any other fresnel design. If you don't have money for a tracking device, you could sit there the whole day with a welding helmet and manually orient the focul point producing heat for your nano greenhouse food production and personal waste recycling of phosphate.
Instead of linkages, mount the heliostats perfectly flat to each other on a steel grid. Each receives the same actuating signal from the Kipp & Zonen tracker, compensating for the slight spatiality in the zenith and azimuth planes, with Harmonic drives. There are multiple ways of actuating the heliostat in the azimuth and zenith planes:
SRI abacus drive is zero backlash but the Harmonic drive company bought the patent, squashing its implementation for the next twenty years. Patents hacking with a Fronting company won't work because anything that scales in the wide sunny open will be shut down with a court order. Any large scale implementation of the abacus drive would be an easily identifiable patent infringement, because the usage hasn't been licensed. Patents are a form of selective communism. Harmonic drive(PTY) impedes solving peak phosphate, as we must recycle sewage with incineration and HCL acid and move all agriculture to airoponics Greenhouses. Multiple rotations(50) of a stepper or dc motor results in a single rotation on a harmonic drive.
Our problem isn't Global warming: carbon is a harmless gas, water vapor makes up 95% of all greenhouse gasses, we are running out of cheap uranium(most carcinogenic) free phosphate. You body consumes a gram of phosphate per day, the stuff is only available from Phalaborwa and Morocco and can be endlessly recycled in a closed loop with a solar furnace or Thorium nuclear reactor instead of washing it down the rivers. Cheap high precision solar trackers will be available, as the patents expire, which ironically will increase So4 pollution as the Fishcer Tropsch process is used to turn the vast amounts of coal into fuel. Energy production will reduce to the cost of scrap metal.

Melt desert sand and pulverize the vitrified sand, conserving sea sand
We are heading to an era of unlimited abundance, one wherein we won't actually have to do slave labor work, but sensible community uplifting work like melting desert sand into vitrified sand, paving our own Mountain bike trails. Lathe milling it into hexagons with a Five axis mill and constructing dome Housing along these trails in the Kalahari desert and creating oasis's along the path watering trees with Atmospheric water harvesting, sucking in a fraction of the vast sea of water vapor that we walk in. https://www.waveswell.com/ ,waveshell vid . There is enough wave power to provide all the worlds electricity, but we don't have the sand for the concrete.

The millions of megawatts it will take to melt desert sand into glass with solar furnaces is transfered into the concrete for the waveshell technology
Ironically banning coking coal as a carbon source makes steal production more expensive, pushing out wavepower technology into the future and producing even more pollution(law of unintended consequences).
Optical_encoders#ring_encoders divides 360degrees into one million positions over full rotation. Couple this to small dc motors and planetary gearbox with PID control for precise positioning. A ring encoder is much more expensive than the Austria AS5148, which provides 4096 positions over full rotation.
http://www.txles.com/technology/ The TEXEL battery technology is based on Metal Hydrides and Hydrogen, and has more than twenty times higher energy density than other heat storage technologies, such as Molten Salt, and competitive with Lithium-Ion. The energy density is predicted to be improved dramatically with future development. The TEXEL battery’s high energy density also opens up for other market segments where space, weight as well as environmental issues matters.
https://web.archive.org/web/20120120143459/http://energytower.org/ This is a project to design and build a system that uses a combination of direct and indirect solar collection to generate electricity and store thermal energy in an economical, environmentally friendly, scalable, reliable, efficient and location independent manner using common construction materials. The project is being managed with a similar methodology to Open Source Software Development and the ideas and contributions are being published openly on the Internet without an attempt to secure patents. The hope is that with an open philosophy that the project shows similar Rapid Application Development and success as Linux and other Open Source Software projects and provides a system that can meet future energy requirements in a sustainable manner.
archive.org model steam turbinedesign pdf
https://www.youtube.com/watch?v=KdFIHecZDfc solar dome heated with solar furnace for water extraction and https://www.youtube.com/watch?v=B9m_jaXCSss. Developed by Cranfield University with kr patent
https://www.solarwaterplc.com/
Machine design
| Make it extreme | Lathe |
|---|---|
 |
 |
https://www.youtube.com/watch?v=uhsgdwUX1-w The world’s first production CVVD engine! CVVD stands for continuously variable valve duration. This technology is currently used in the 1.6L turbo engine of the 2020 Hyundai Sonata. In order to understand it we need to understand how valves work on an engine.
- quantum tech youtube cnc pipe bender
3d printing
Heated chamber Stratasys patents prevents you from printing Mountain bikes without a Fronting company.(patent expired Apr.2021)
Wireless and Fixed wired
- wireless and wired,
- MeshNetworking documents the https://locustworld.com/ mesh technology such as WiaNa
- Free space optics
- Gprs and wifi streaming rtsp-simple-server is a simple, ready-to-use and zero-dependency RTSP server and RTSP proxy, a software that allows multiple users to publish, read and proxy live video and audio streams over time, written in Golang.
Ez-WifiBroadcast is a bidirectional data link using commercial off-the-shelf hardware like WiFi modules and a pair of Raspberry pi computers. Coupled with special software this unique system allows transmission of low latency HD video, telemetry and control data between endpoints. In comparison to a classical wireless connection Ez-WifiBroadcast tries to imitate the famous properties of an analog link like graceful signal degradation and no association between the endpoints.
Guns
Connect industrial Quick Release Exhaust Valves(Pepperball wyz228g youtube in parallel, modding the concept from the Air Engine idea, where multiple fire extinguishers pressurized to only 10Bar release their energy in sync driving a turbine. This will allow a CO2 Crossbow arrow speed boost from 400ft/s to 1400ft/s.(arrow is placed over a pipe , the crossbow design has Patents.
https://www.youtube.com/watch?v=SGMTEOcCyZw This is a full tutorial that teaches you how to make expensive airbows at home, from simple parts you can order from amazon. While the homemade weapon can not come close to the ease of use of the FXAirguns products, it does outperform each and every commercially available crossbow or airbow we have ever seen.
- https://www.youtube.com/watch?v=fz6cMwl4BvE Homemade Pneumatic Concrete Nail Gun
- https://www.youtube.com/watch?v=cBazTqyIp2w colin furze pneumatic cannon for his screw tank build linked form Xrobots
- https://www.youtube.com/watch?v=4I-p8vjQ95s&ab_channel=SmarterEveryDay 1000mph pressure gun launching baseball.
Alarm systems

spotterrf.com radar for 1.4km radius farm surveillance.
Radar#RCWL-0516_RCWL modules in red silicon around a perimeter. They are 3.3ghz colpitts oscillators that will activate should they be jammed. https://sasecurity.fandom.com/wiki/Category:Grounding mount all electronics on metal plate(OutdoorBox) with two fans for humidity control. The plate is tied to earth ground, preventing static electric charge buildup from the fans. Paint the OSP box with copper paint(Farraday cage) preventing rf leakage unto nearby radio modems and insert copper clad PCBs between PCI wifi cards on the motherboard. Melted silicon glue around PCI slots prevents corrosion caused by weather. RAM slots also a source of problems due to corrosion by time if weather humidity is high. Make usb wifi dongles directional with mechanics ligth by painting the ML with copper paint and positioning the dongle near the focal point. Avoid using omni antennas as they cause spectrum pollution and worsens existing pollution by absorbing and radiating it back again. Copper pcb behind the RCWL radar model, making it 180 and not 360 as it detects movement through windows. Use mechanics light for directional beam, 3d printed and copper painted. GPRS modem, GPS and IMU gyro built into shoe.
Twist right foot more than 80 degrees to indicate distress call to base station, if periodic ping is lost, dispatches response to last known GPS position. Suitable for both indoors and outdoors. If you are forced to lie on the ground on the kitchen for example the IMU detects the shoe orientation and sends alert. Use both a paint solution and pepper spray against intruder with gas mask. Install military grade gas masks in every room, welding gas masks won't work.
If an intruder forces you to open a safe, take him to a cubboard, safe or door that is never opened. If openend, an alert level 10 is activated, sending out a distress call. Make certain that a fair amount of cash is in such a safe, intruders are enraged if nothing is found, you're playing for time. False alarms are dealt with by linking each distress signal to an Ethereum contract: if false alarms become your problem, then you will make certain to minimize them.
| Razor wire DIY make your own. |
| Lidar for home security, processing of objects in the point cloud. Use ir and ultrasonic range modules in conjunction with door contact switches. |
| VehicleSecurity. |
| https://www.youtube.com/watch?v=_DApAb12xyQ life like masks can be custom made for impersonation, positive identification must be combined with Pose estimation gait analysis(25 data points are unique to each individual) of a person for positive identification. |
Housing
 |
Greenhouse. Use Pose_estimation#nvidia_labs and lane detection robots to UV radiate strawberries at night against milldew infection and pick them when ripe with Chris Annin six axis robot. Annin doesn't allow commercial applications but this amounts to a software patent, which isn't enforceable in South Africa. |
| Liquid nano clay , Pollution , farmbot | |
| https://www.youtube.com/watch?v=s_gu-VriMPo 3d print house with sodium silicate and soil. | |
| wasp printing Cob house printing automation, prints with straw, clay and sand mixture. | |
| https://www.youtube.com/watch?v=YfOmlZD4BRk Workshop on Juncao Technology Project of China-UN Peace and Development Trust Fund |
https://www.youtube.com/watch?v=gxbyWly_pls 3d printed houses by matt farrell
Sports

steering bolted, not welded between two frames. Allows for its suitcase transport.
GPL proprietary code
GPL,BSD and MSFT end user license is defined as proprietary by copyright law. A physical property is leased under contract law, IP is licenced under contract law. Each legal jurisdiction determines what tangible and intangible asset can be leased and licenced. In Scotland the owner of the property even owns the section of river that runs through it, while in South Africa all rivers belong to the state who in turn allows anyone passage via it. IP enforceability, how it could for example strip you of your patent rights as Apache2 does is dependant on a legal jurisdiction.
Patents , GPL and BSD The GPL restriction from the copyright holders are used to emulate the effect of patents. Apache2 contract means that the licensor proprietor hasn't exempted anyone from his patents, only that the licensees have on all their past, present and future patents. Opensource proprietary code are not really "licenses" but contracts incorporating both patent and copyright law per relevant legal jurisdiction. It is defined as proprietary code licensed for restricted usage by the licensees, in almost all cases, it like a patent involves the revealment of all details. The usage is licensed under contract law(this is fuzzy), much of the GPL terms aren't enforceable in South Africa. https://github.com/martinruenz/maskfusion/blob/master/LICENSE-ElasticFusion.txt, no commercial gain is allowed making Elastic a de facto software patent, which ZA law doesn't recognize. You can no more have a "fiat currency"(USD) then you can be fiatly pregnant:bitcoin is a crypto commodity, a currency is defined as a letter of credit by a sovereign nation state. By the law of excluded middle(binary opposites) something is either public domain or under proprietorship(patents,copyright). The entire Internet has conspired to make this fundamental usage of laws of logic impossible for most to grasp.
"....http://www.fourwalledcubicle.com/LUFA.php Commercial entities can pay a one-time US$1500 fee to obtain a commercial license to use LUFA in their products...." opensource license(modified MIT and https://www.freertos.org/a00114.html#commercial
https://www.gnu.org/philosophy/free-sw.html None of the restrictions apply to FSF themselves as they are the proprietors of their GPL licensed code. They use the term "free" over fifty times, misdirect you away from the fact that they are paid lots of money by corporations who use their GPL proprietary software, exempting them from the licensing terms.
NPA won't prosecute ICASA directives
Sa Telecoms licensing, 5G Icasa, telecom operators can't prosecute anyone, only the NPA can do this and they won't on anything except SABC and Mhz radio spectrum. there is no criminal prosecution for example on using the 1Ghz spectrum, neither will there be any, since it won't ever be allocated for any use.
- https://medium.com/indrastra/overview-the-economics-of-releasing-the-v-band-and-e-band-spectrum-in-india-8d042c900032"...Availability of additional spectrum is an important piece of this puzzle. V-band (57 GHz — 64 GHz) and E-band(71–76 GHz and 81–86 GHz) are two microwave bands which can be useful for bridging this need for additional spectrum. Spectrum in these bands can be used for high capacity data transmissions for last mile connectivity over short distances ranging from 200 meters to 3 km. These bands can be put to a variety of backhaul (i.e. for connecting towers). V-band can also be used for access under the Wi-Gig standards..."
South Africa is the only country in this universe where you can tack on the 5G physical layer on to any frequency above 1Ghz and not be prosecuted by the National prosecuting authority. Even 2.4ghz because it is defined as license free, which means do whatever you want, there wont' be any criminal prosecution, else you wind up with a precedent and pretext to shut down all communications not sanctioned by cellphone companies who are nothing else but legal firms with an antenna on their roof.
Object oriented hoax
oop will go down as one of the biggest academic fraud's perpetrated on society. |
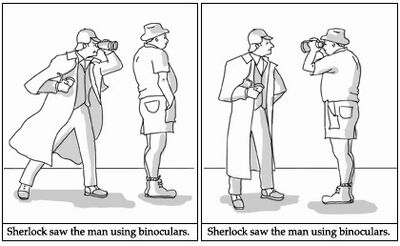
"...we fight the bewitchment of our intellect by the use of language .." Wittgenstein.(The Sherlock caption is known as a "structural ambiguity" in linguistics. It illustrates that words and sentences have no meaning whatsoever: You have a green light. What does it mean?
"...And the profession is now guarded by a priest class that benefits from OOP's murk and mystery—the fewer people who can communicate with computers, the more secure their jobs..." ,..."...If you are new to OOP, please don't be fooled by simplistic examples. These bait-and-switch examples often take the form of geometric shapes, animal categories, vehicle taxonomies, vehicle parts, employee types, Y2K dates, stacks, device drivers, clothing, or bank account examples...." Richard Mansfield(Mansfield proposes Table Oriented Programming)
OOP technology has generated more confusion than almost any other computer technology. For example, many OOP "experts" claim that most companies are either not using OOP properly(you're to stupid,No true Scotsman fallacy), or are not taking advantage of OOP.(double speak1, double speak2)
Oop(object oriented programming) is category error or category mistake: Nouns,metaphors, "behavior", verbs, rocks and fields of mielies don't exist inside of computers, its only purpose is to map inputs to outputs(local and global variables), like a math function maps the domain to the range. Perl6(raku) exemplifies this confusion, "structurally ambiguating" with the term "behavior" between actual behavior in the real world and its alternative meaning as a computer function inside a struct(taking the struct itself as its firs parameter), mapping inputs to outputs.
Oop stuffs procedures into structs(classes), implementation is hashmaps with instantiated context-sensitive namespacing. The procedures are either inside("behavior") or outside the struct, it fundamentally remains procedural programming because of the ontology of the computer.
Oop are structs(collection of data types) with functions, where each function's first argument(self in Python and this in Java) is the struct(object) itself and dot notation makes this implicit, making the "object" a restricted global. This isn't an "abstraction" but a particularity, hard problems in unstuffed procedural programming becomes impossible to solve when those same functions are embedded inside the struct. (commentry on Dan saks). Which is situation that Dijkstra describes as "..an exceptionally bad idea...", Rob Pike the "...Roman numerals of computing.." and Torvalds on C++ as "idiotic". The "state" is how the variables of the instantiated class(object) changes as the functions which take the struct as its first parameter modifies it. See cs.stackexchange.
The functions inside the sturct are tied in leg irons to a collection of data types, a situation that Armstrong describes as wanting a banana but getting the gorilla and entire jungle with it. Erlang's concept of a "message" can only be some sort of a struct without the function stuffed inside of it.
"... behaviour and state, these terms are almost completely meaningless ..." Rich Hickey inventor of functional programming language Clojure
How many design patterns bridge jungles of bananad state with static methods(bridging pattern)? Interfaces are kludges to work around the fact that multiple inheritance is broken(with the exception of maybe Eiffel but your Firefox browser will take 5min to boot if written in Eiffel). An interface is a struct without data types and only functions inside of it or "behavior" as our "software engineers" likes to call procedures.
Niklaus wirth ....Nevertheless, the careful observer may wonder, where the core of the new paradigm would hide, what was the essential difference to the traditional view of programming. After all, the old cornerstones of procedural programming reappear, albeit embedded in a new terminology: Objects are records, classes are types, methods are procedures, and sending a method is equivalent to calling a procedure. True, records now consist of data fields and, in addition, methods; and true, the feature called inheritance allows the construction of heterogeneous data structures, useful also without object-orientation. Was this change of terminology expressing an essential paradigm shift, or was it a vehicle for gaining attention, a “sales trick”? ..."
Haskell's monads are a means of dealing with global state in functional programming. Monads deals with the global state that daisy chaining multiple functions have, as each function transforms its associate struct. Both functional programming(monads) and oop(abstract factory pattern) implement https://en.wikipedia.org/wiki/Currying, monads hides dealing with global state, basically a Design patterns for dealing with it. With plain procedural the structs and functions are separate like life and death itself, Currying daisy chains functions and their associated structs in a such a way that only if you understand the math of currying are you able to separate them back through the thicket of global state. Terms like "factory pattern" directs one away from this. The embedding of the function inside the struct was the ruse used in order to turn programming into the domain of honours degree mathematics, limiting the supply of programmers.
"....They are solving problems that they created themselves. I wrote many advanced functional programs that very few people can write... functional programming collapses under its own weight like the attempt to sort everything under set theory, the complexity scales beyond the human mind's capabilities...hard problems become impossible to solve..."Yin Wang on Haskell
You no more need to Curry your functions when writing and ERP or CAD program then you need to think through lambda calculus when making coffee and tea. Creating category mistakes such as deriving cats and dogs from the "mammalian struct" was meant to compound the confusion and steer you away from getting the needed Real Analysis etc. background to grasp the visitor pattern etc at a honours degree math level. This is why the Wikipedia articles on design patterns are incomprehensible since it verbiages complex but exact mathematical descriptions into a metaphorical goo.
My math background made me realize that each object could have several algebras associated with it, and there could be families of these, and that these would be very very useful.” ~ Alan Kay
"Abstract Factory pattern" getting "reverse dependency injected" via polymorphiated "operator overloading" templified by the template class wordifies global state into the world of Banach spaces, Hilbert trasforms, Currying(category theory) and functional analysis. This math in turn is used to reconstrue this contrived problem of global state spawned by having the functions inside the struct all have global access to this struct by taking it as its first parameter back into a pseudo local state: only mathematicians can grasp functional and oop.
Oop concedere.net while metaphor is essential to language it happens to be completely absent in mathematics and programming. There are no metaphors at all in software and this is exactly why building software is so hard.
Mammals,rocks,fudge, mielies,rats, software engineers,fleas, cats and dogs inside a struct without a function inside the same struct(taking the struct as its first parameter) is defined as procedural programming. A struct as a collection of datatypes has nothing to do with how our volitionalism expresses interactions in the real world: the world of dogs and cats doesn't exist in either struct stuffed procedural(oop) or unstuffed procedural programming, not even metaphorically which we use to explore the unknown. Attempting to derive cats and dogs from mammals inside a struct is like attempting to derive the marital status of the number seven, it's a category mistake. Hence no syllogism is possible to resolve the arbitrary derivation of cats and dogs from mammals in the procedural to oop transition. Classification schemes like SRP(Single Responsibility Principle) etc. injects a model into the problem space of mapping inputs to outputs which doesn't exist. Robert Martin concocts this so he can solve a contrived problem and make money out of it, he doesn't want to code.
From a Perl perspective (perl iteration) Design patterns turns a programmer into a fancy macro processor, by using polysemic pretentious language in a reverse Nigerian prince psyops. The grammatical gargoyleism of advance fee frauds hone in on the most obtuse of society: with high cognition "software engineers" a metaphorically induced category mistake cloud how the ontology grounds the epistemology(the nature of existence determines the nature of knowledge).
You might wonder how could STEM computer scientists be so philosophically confused about category mistakes. Take for example Robert Sapolsky a biology professor who believes that the mind is conjuring trick created by natural selection. The statement itself was created by his mind, why should we then believe anything from a person who believes he is purposeless purpose?
Vlang is going to be the one language to rule them all: Multiple variations of Currying such as Elixir, Erlang, Cpp, Elm etc. is restricts the pool of talent even further and pushes Vlang's adoption as the only programming language we need out by years.
Niklaus wirth "....However, the core of the idea is that functions inherently have no state. This implies that there are no variables and no assignments.....This yields an extremely high degree of storage recycling; a garbage collector is the necessary ingredient. An implementation without automatic garbage collection is unthinkable. To postulate a state-less model of computation on top of a machinery whose most eminent characteristic is state, seems to be an odd idea, to say the least....They have introduced state (and variables) in various tricky ways. The purely functional character has thereby been compromised and sacrificed. The old terminology has become deceiving...."
Garbage collection is also a malware attack vector(Handmade hero).
Dan Saks, whom we should view the same way Schopenhauer viewed Hegel, contributed to ungrammatical behemoth that is C++ by serving on its ISO standards committee so that he can make money by tutoring and consulting gigs. C++ is like legal documents contrivedto be impossible to understand with common sense. Combined with the CIA Systemd trojan, computers are becoming black boxes, preventing actors from creating cruise missiles with Nvidia Jetsons but also making it impossible to certify a self driving car without Red Hat's involvement. All attempts at creating drone attacks in Germany have been intercepted, Systemd is part of the reason. The primary purpose though of systemd is to turn Linux into a de facto Patents. Remember when way back IBM went around demanding money from tech companies for using its patents? Well now it can emulate the same by demanding than any commercial venture release all their source code, since all code eventually has to use the mount command and kernel code entangled with systemd under GPL2.
Words like “abstract”, “pattern”, and “object oriented” are used like a shield to protect the implementer from critical words like ... “complicated”, “obtuse”, and “annoying” Indirection isn't abstraction(zedsaw.com)
Functional programming attempts to model the world using lambda calculus, but you can't model for example relational databases with lambda calculus. Thinking through a linear sequence of steps when making coffee in the real world with lambda calculus is like like living in a world where your sense perceptions are not fed to you via the electromagnetic spectrum but with fiber pipes(monads) wired directly through your skull into your brain. Nobody views the process of making coffee in terms of lambda calculus or the boolian logic of sql.
Oop breaks up the problem of mapping inputs to outputs with procedures into data types. In the real world you make one cup of coffee(int) with water(float), milk(float), brown powder(float) and a kettle(int). Now instead of describing this process in your program as a linear sequence of verb(Nouns and verbs oop) like steps, instead with Oop you break the process up into noun like “data types": white and brown -> grey with red translucence.. Thinking through math of Currying with Oop and Monads takes you from a natural verb like existence into a state of nounness: professing themselves to be “software engineers” they have become pretentious verb inverters. See https://news.ycombinator.com/item?id=11952506
You might have a good model of the world, but the constraint is the ontology of the computer like the L2 cache event. Oop consumes up to 90% of the L2 cache cycles because the compiler can't optimize for the function calls stuffed inside the struct: reality isn't a hack you are forced to deal with to solve your problem, it's your actual problem(Mike Acton).
With the three paradigms of lambda (functional), struct stuffed procedural(oop) and procedural we attempt to model the world the way we see the world: a binary succession of ideas. Zeno's and Sorites paradoxes asks what is in between these binary events. When Zeno attempted to grab hold of the space between Achilles and the tortoise,he grabbed hold of the law of excluded middle. The paradoxes arises due the reification of the laws of logic, these laws can't be verified as any verification would have to use the same laws and the paradoxes resurface each generation under a different rubric.
Applying Popper falsification to the laws of logic would be a category mistake: the laws of logic are unfalsifiable by necessity, as this enables ratiocination about what is falsifiable and prevents Agrippian regress of falsifiability. "...Science vs Religion..." is also a category mistake. Popper's idea of falsifiability was recognized by Richard Owen, Samuel Butler and Charles Hodge in their critiques of Darwin.
Behe's Irreducible Complexity is a variation of Sorites paradox of the heap: when does a hole in the ground become a mouse trap, when does an indention become a hole? How much soil must you remove from a flat surface before you get a hole. A mouse trap, whether of a single element or multiple elements exists only as a Berkeleyan idea. We only have particular ideas, not abstract ideas, abstractions don't exist. Close your eyes and imagine anything, what did you see? You saw tigers and horses and things, even maybe the word 'abstract' plastered across the Aurora Borealis but not abstractions, only particulars.
Zeno's paradoxes as it relates to Irreducible Complexity must be seen through the syllogism:
- Axioms are based on induction.
- Deduction uses axioms.
- Deduction is based on induction: even Godel's incompleteness theorems are entombed within Hume's circle.
1+1=2 is an axiom based on our inductive experience of placing two rocks on a table. To say that the axioms of a system isn't provable within the system by the same axioms, is to say that our experiences aren't referential within the system of our experiences, it needs to refer to something outside of the system for its justification. Science(the art of measurement) is a dissimilar term for induction, which is used, not experienced as the future hasn't been experienced Our experiences and usage of induction(science) are encircled by Agrippa, entombed by Hume , with Hempels raven perched on top: laws of nature or laws of science don't exist in contrast to the laws of logic. Before the arrival of human minds the universe couldn't have existed and not existed in the same manner, this would violate the law of non contradiction. Our belief in the laws of logic are religious beliefs, just as religious as our usage of induction.
Alexander Pope addressed Irreducible complexity and being a friend of George Berkeley, his ideas could probably be found in Berkeley's works. Aristotle reflected Zeno's concept with constituted spontaneity(from Darwin's OoS) and D'Arcy Thompson preempted Behe's IC with composite integrity. With our volitionalistic language we project our presuppositions into the Zeno, Sorites debates as arrows,sand,mud, millets and tortoises are joined with mouse traps. Gould's punctuated equilibrium vs Darwin's gradualism view on evolution(adaptation) is also a take on Zeno. Darwin projected his belief in slow social change and Gould his Marxism, an idea that traces back to Hegel's projection of the Enūma Eliš mythological archetype. Adaptationism like every other belief from finite knowledge is a conclusion in need of a syllogism.
Oop has given the term "procedural" a PR problem, hence Dave West tries to enunciate it under the rubric of Data oriented design. Paparazzi uav and the Gentlenav UAV project achieves control through interrupt driven plain procedural C coding, while Diydrones arducopter stuffed their PID control procedures into structs, making it difficult to discern what the data means(Mike Acton).
Cpp was invented (Stroustrup), Alan Kay so that arbitrary code is executed in the cpu with each object instantiation(virtual functions and virtual tables), allowing for endless hacking of Apache databases, providing the top500 with a competitive edge as the trade secrets are exfiltrated via MINIX and ultrasonic pulseaudio. Sharing of the data occurs each year at NSA headquarters under the rubric of "cyber security".
That crackling sound the speakers make when pulseaudio consumes 30% of cpu cycles is when an ultrasonic link is established between your cell phone and the pc. Anti virus programs are so effective at finding "viruses" because the viruses are written by the KGB(Kaspersky) and CIA(injected into the chip itself at the foundry) so that their Trojans(McAfee) can extract all the hdd data without raising suspicion. Many virus writers who didn't get the memo that only the KGB and CIA are allowed to encrypt hdds and exfiltrate data were sent to jail. Not all though, hackers and credit card thieves are allowed a moderate form of activity as a distraction from what is actually going on.
All operating systems install on top of MINIX, which will only allow Wireshark and Snort to see packets it wants it see. Hardening the OS with iptables etc. signals to MINIX an attempt at hiding data. All programs of any size and complexity must be a set of procedures and single hashmap storing the global variables. If you still can't solve your problem, then it's beyond the ontological domain of silicon based input output mapping.
Oop allows for embezzlement in ERP software, there is a reason why git is written in plain C(Torvalds on C++) and Eric Raymond's reposurgeon in golang without oop. The designer and writer of ZeroMQ regrets writing it in C++ instead of C coding.
never use getter and setter methods youtube video and new,delete,malloc in c++ wraps the malloc in a single command. The software design team with their $1.5 trillion F35 program and the welders at Eskom sabotaging the boilers have the same desire: lifelong employment. jaron lanier
links
inventions test page political and ecological events


